ColorTokens
Colortokens is a cybersecurity company specializing in providing zero-trust solutions for enterprises. It offers advanced security measures by segmenting and securing networks, applications, and workloads, reducing the risk of cyber threats. Colortokens' approach allows for granular control over access and security policies, helping organizations protect against breaches and ensure compliance with regulations. Their services are designed to be adaptable and scalable, catering to the needs of both small and large businesses.
More Infomation : www.colortokens.com

Enterprise
Microsegmentation Platform
Xshield stops the lateral spread of malware & ransomware by putting a micro-perimeter around every network asset.
The Xshield Difference
Actionable Visibility
Multi-dimensional visualization of critical assets to plan your cyber defense
Multi-dimensional visualization of critical assets to plan your cyber defense
Real-Time Risk Measurement
Security posture reports for you and your stakeholders
Security posture reports for you and your stakeholders
Comprehensive Microsegmentation
Protection for all asset types, IT, IoT, and OT, on-campus, and in the cloud
Protection for all asset types, IT, IoT, and OT, on-campus, and in the cloud

Immediate Security and Continuous Improvements
Reduce your risk in days not months
Reduce your risk in days not months
Your Path to Successful Microsegmentation

Guided Workflows
Quickly define policies that stop unauthorized traffic using templates for repeatability and accuracy, with automatic policy recommendation using heuristics.
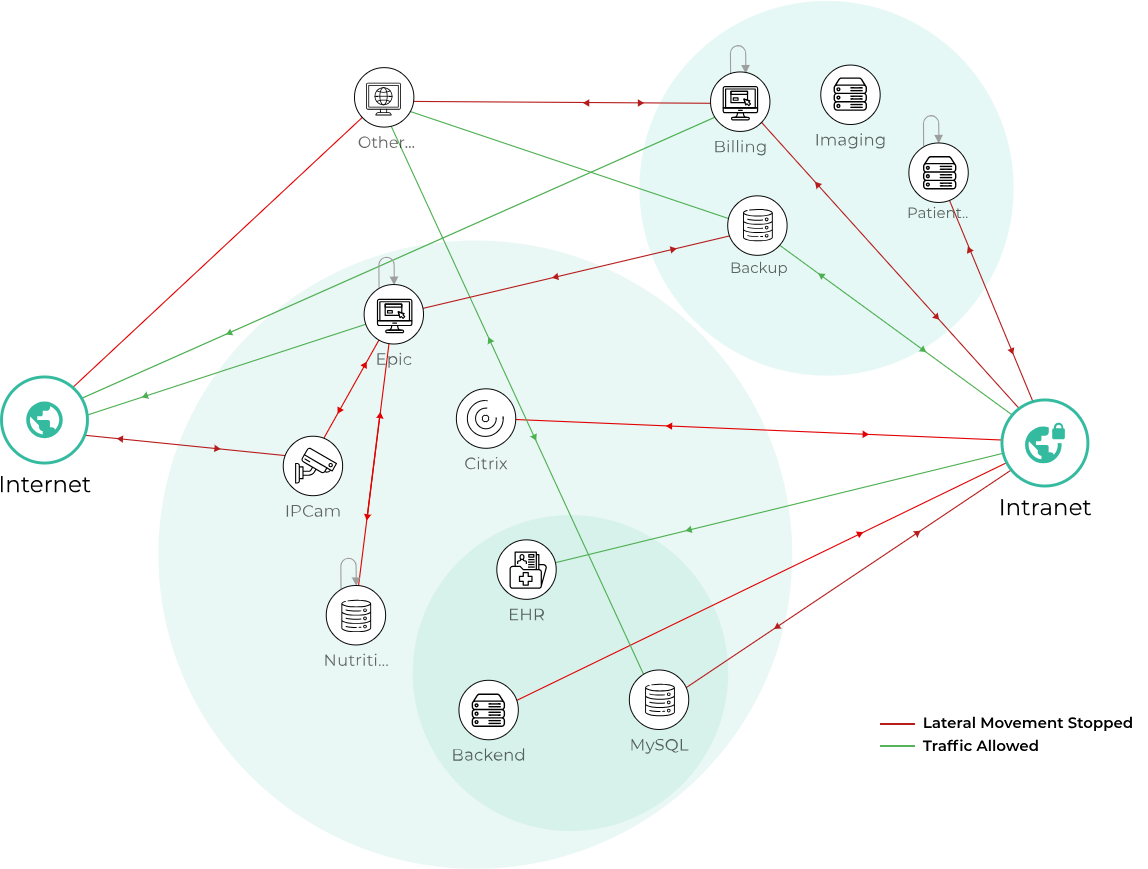
Visualize and analyze your landscape globally with multiple dimensions and filters, for more precise and secure policies.
Quickly define policies that stop unauthorized traffic using templates for repeatability and accuracy, with automatic policy recommendation using heuristics.
Visualize and analyze your landscape globally with multiple dimensions and filters, for more precise and secure policies.
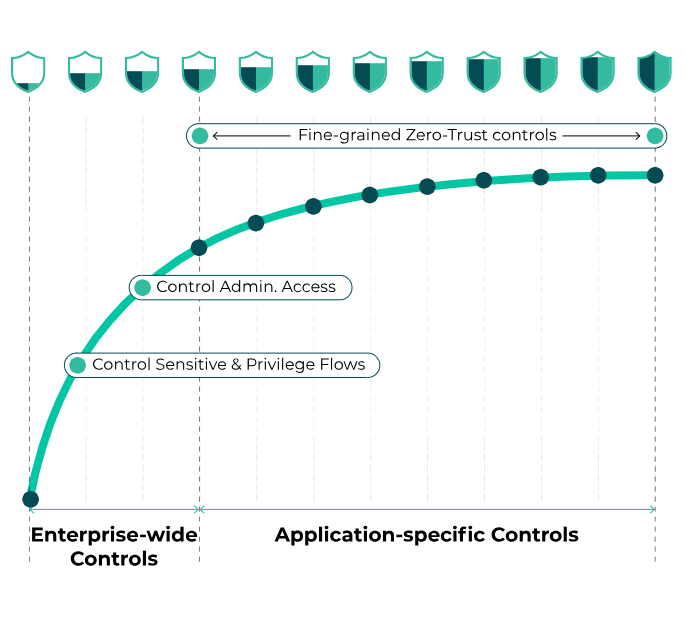
Continuous Risk Reduction
Quick start your cyber defense with an innovative approach that immediately improves your security with enterprise-wide controls, then progresses to application-specific zero-trust controls.
Quick start your cyber defense with an innovative approach that immediately improves your security with enterprise-wide controls, then progresses to application-specific zero-trust controls.
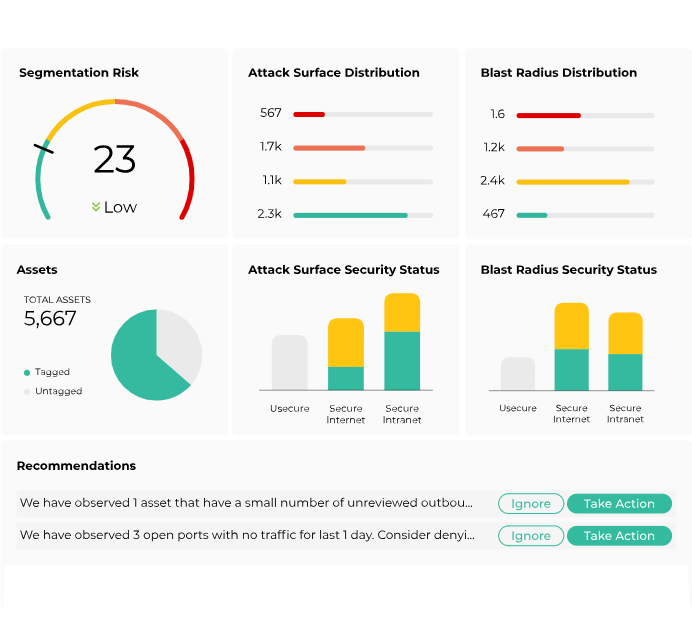
Risk-Based Dashboards
View security posture and communicate improvements with stakeholders
View security posture and communicate improvements with stakeholders
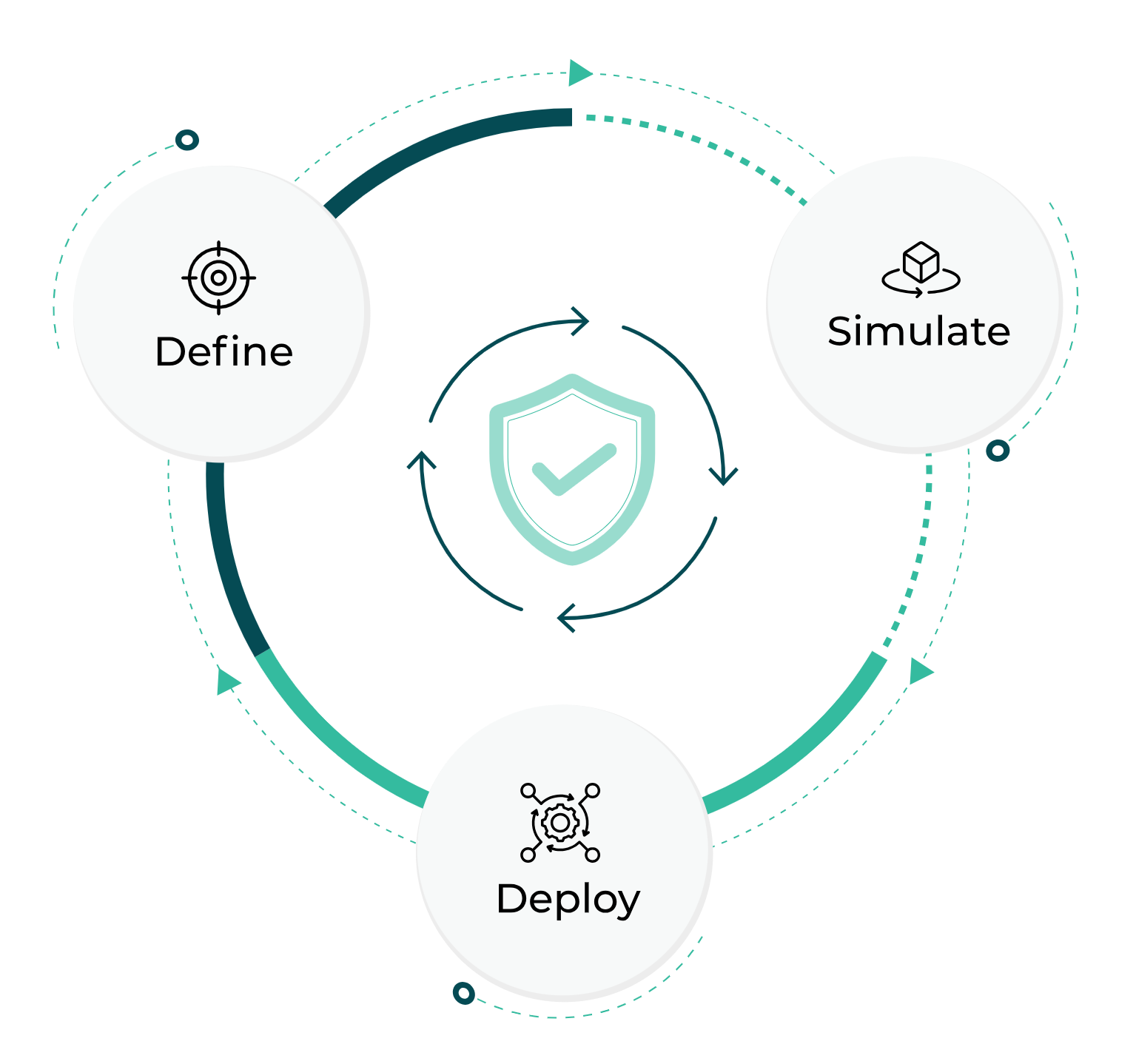
Non-Disruptive Implementation
Simulate policies to validate them before enforcement.
Simulate policies to validate them before enforcement.
Platform Capabilities
Auto-Tagging
Simplifies asset tagging using custom rule-based criteria

Template-Driven Policy
Enables consistency, and facilitates the addition of new assets
Visual Policy Design
Provides a network map to define approved/denied flows
Policy Auto-Recommendation
Suggests policy based on observed traffic and heuristics
Integrations
Leverages investments in SIEM, SOAR, Vulnerability DB, Threat Intelligence
On-Device Policy Testing
Validates policies before enforcement for non-disruptive implementation

Container Microsegmentation
Controls Kubernetes communications at the API-level

Operational Technology/IoT Microsegmentation
Provides traffic visualization, simulation and agentless enforcement
